Bug Bounty Hunting

Bug Bounty is a strategy for discovering vulnerabilities on a website. Because a website is the public interface of your business, as more features are added to it, it may become more exposed. it is important for security team to perform stress and fuzz testing on website and find critical vulnerabilities. Security must be implemented on each layer of application, website are placed on top of these layers. Incase website is vulnerable it can also give system level access to attacker and disclose sensitive information.
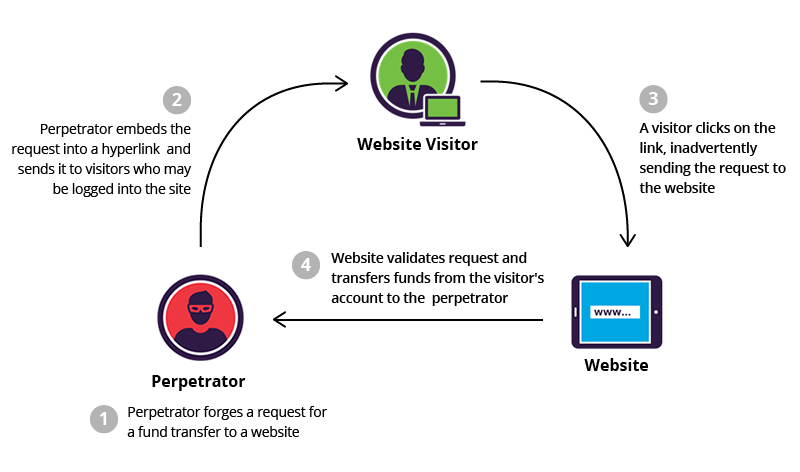
Cross-Site Request Forgery (CSRF) is a technique that induces authorised users to send a request to a Web app that they have been already authorized against. CSRF exploits take advantage of a Web application's confidence in an authorised user. It is a sort of attack where an end user is forced to do undesired activities on a web app in that they are currently authorised.
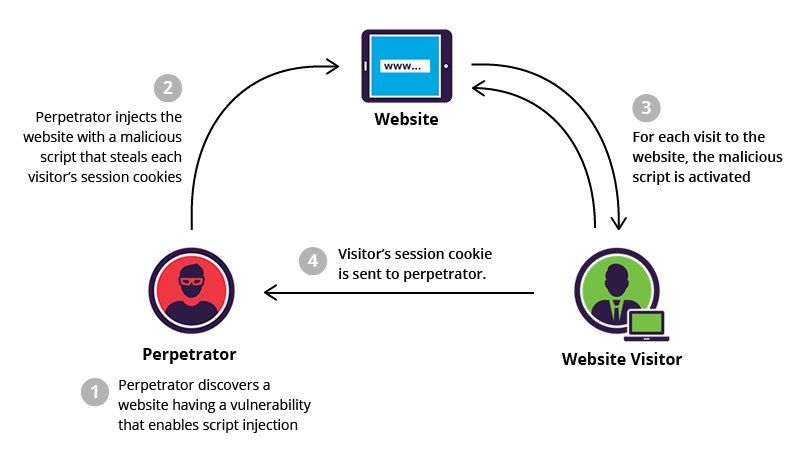
XSS (Cross Site Scripting) occurs when an attacker utilises a web app to transmit malicious script to a separate end user, often in the style of a browser based scripts. The vulnerabilities which permit such exploits to operate are fairly common, and they occur whenever a webservice incorporates input validation inside the output it creates without verifying or encapsulating it.
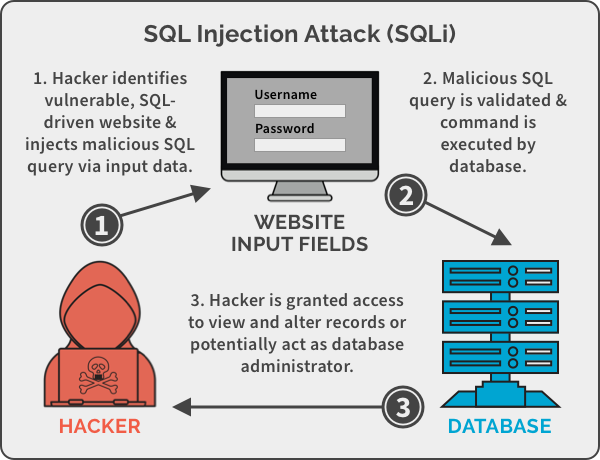
SQL injection, often known as SQLI, is a popular attack method that employs harmful Sql queries to manipulate backend databases in order to obtain information that's not supposed to be shown. This info might contain confidential corporate data, users lists, or confidential consumer information.
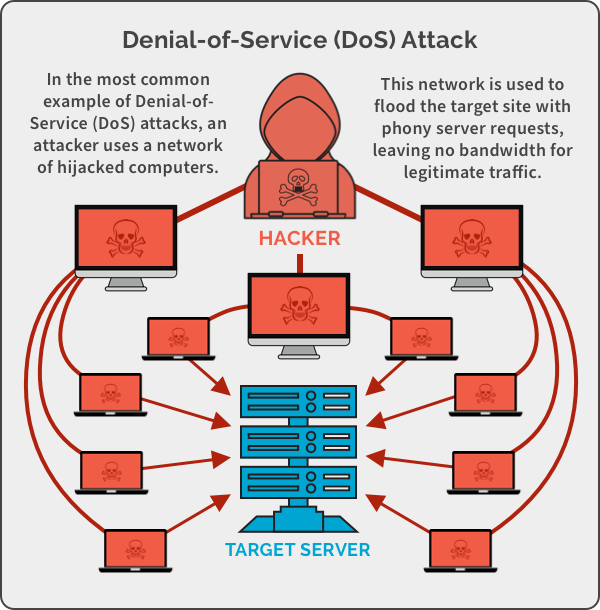
A denial-of-service scenario is created by bombarding the targets system or networks with traffic till the victim is unable to react or fails completely, prohibiting genuine users from gaining access. DoS attacks could result in significant losses either effort / expense since its services and facilities are unavailable.
Course Modules
» Burp Suite Customization (Writing Own Extensions)
» Introduction to Web-Assemblies (WASM)
» ASP.NET & PHP Deserialization
» Exploitation of PHP using own PoC
» Bypassing Auth0 and Specialized Tokens
» RCE and RFI
» NoSQL Injection Attack
» Poisoning Database via XML
» IDOR Attacks
» Arbitrary Commands Execution/Shell Injection
» Report vulnerability and Generating reports using tools

